Share this
Previous story
← No CISO? Healthcare Orgs Stall on Best Practices
A NIST Cybersecurity Framework 2.0 Core discussion draft was released in April 2023 (see ref 1 below) — the latest event on the timeline for updating to NIST Cybersecurity Framework 2.0.
The National Institute of Standards and Technology's (NIST) Cybersecurity Framework (CSF) version 2.0 (NIST CSF 2.0 for simplicity) provides guidelines and best practices for organizations to manage and reduce cybersecurity risks. The goal of NIST 2.0 (and previously for versions 1.0 and 1.1) is to protect critical infrastructure, encourage a culture of continuous cybersecurity improvement, and strengthen the security posture of all organizations.
The CSF builds on existing standards, guidelines, and best practices for organizations to manage and reduce cybersecurity risks. It has played an important role in improving the cybersecurity posture of businesses, healthcare providers, and in government at all levels (Local, Tribal, State, and Federal). It has also seen wide adoption outside the US as a foundational framework on which to build robust cybersecurity defenses.
As the threat landscape has evolved and experience has highlighted potential gaps in the existing CSF, the need for an updated version has become apparent. NIST CSF 2.0 is that update. NIST encourages feedback from all interested parties so that the draft framework gets refined, improved, and evolves in response to a public-private dialogue. See ref 2 for a link to NIST's information on how to participate in the updating process for CSF 2.0.
NIST intends to complete the updating process for CSF 2.0 during the remainder of 2023 and then publish CSF 2.0 in early 2024 (ref 3). The diagram below from the NIST website shows the timeline — it is currently on target with the April 2023 Core draft release last week.

Diagram 1: The NIST CSF 2.0 Update Process Timeline (Source: NIST (ref 3)
The CSF 2.0 Core discussion draft released for review and comments in April 2023 is a significant part of CSF 2.0, but it is not the only document released. A CSF 2.0 Concept Paper was released as a draft in January 2023 (ref 4). Interested parties are encouraged to continue to comment on the Concept paper and now also on the Core discussion draft.
CSF 2.0 Core has 6 Function sections plus 21 categories. These categories get further divided in the CSF 2.0 core paper, but we won't go that deep in this article (see Table 3 in the Core paper at ref 1 for the details). Instead, we'll outline the 6 Core Functions and 21 categories and also encourage you to read the linked NIST information and participate in the comments and feedback process so that we can collectively ensure that the final CSF 2.0 is as good as possible.
Diagram 2 below shows the CSF 2.0 Core functions and categories as described in the draft (ref 1).
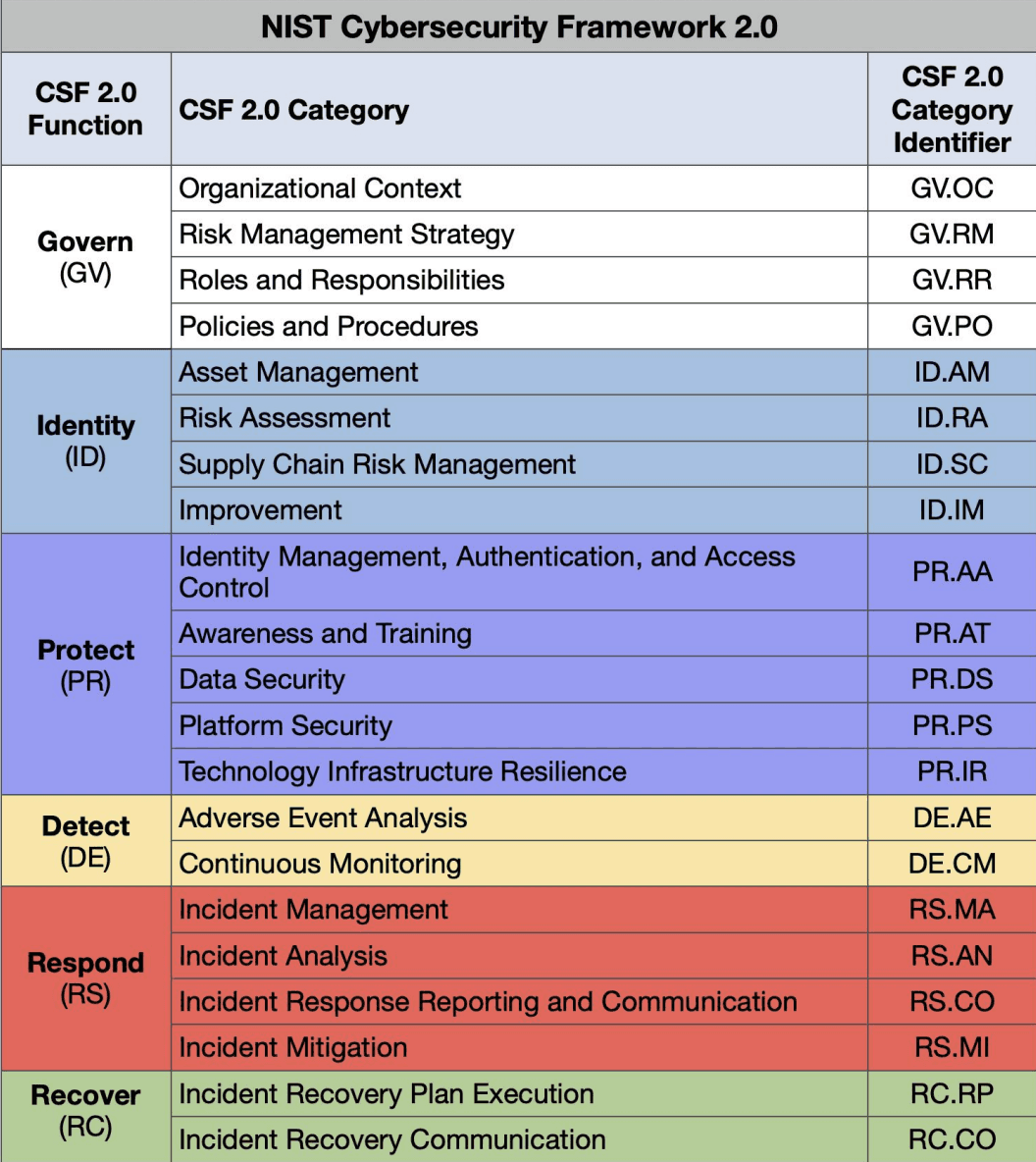
Diagram 2: NIST CSF 2.0 Functions & Categories (source data from ref 1)
The updated CSF 2.0 Core discussion paper builds on CSF 1.1. It has both large and small changes reflected in various reordering, merging, and modifications of the cybersecurity outcomes of the framework. CSF 2.0 increases focus on the following areas:
See the Core discussion draft paper (ref 1) for more details. You can also chat with your contacts at Critical Insight to get an overview of the changes and guidance on what they mean for your organization. Use the contact form below if you don't have an existing relationship with the Critical Insight team.
The release of the CSF 2.0 Core discussion draft is an important milestone on the path to NIST CSF 2.0. We encourage everyone with a stake in protecting critical infrastructure and assets in public and private organizations to read the draft, formulate your thoughts and respond to the consultation using the channels described in ref 2. The more comprehensive the response, the better the final CSF 2.0 will be.
NIST: Discussion Draft of the NIST Cybersecurity Framework 2.0 Core (PDF) - https://www.nist.gov/system/files/documents/2023/04/24/NIST%20Cybersecurity%20Framework%202.0%20Core%20Discussion%20Draft%204-2023%20final.pdf
NIST: Update Process for Cybersecurity Framework (PDF) - https://www.nist.gov/system/files/documents/2022/10/03/NIST_CSF_update_Fact_Sheet.pdf
NIST: Updating the NIST Cybersecurity Framework – Journey To CSF 2.0 - https://www.nist.gov/cyberframework/updating-nist-cybersecurity-framework-journey-csf-20
NIST: NIST Cybersecurity Framework 2.0 Concept Paper: Potential Significant Updates to the Cybersecurity Framework (PDF) - https://www.nist.gov/system/files/documents/2023/01/19/CSF_2.0_Concept_Paper_01-18-23.pdf